SharpExec - Lateral Movement With Your Favorite .NET Bling
TL;DR:
SharpExec is an offensive security C# tool designed to aid with lateral movement. While the techniques used are not groundbreaking or new by any means, every environment is different and what works for one situation might not work for the next. This tool is a combination of code I have been using over the years when needing to move laterally in a Windows environment and due to various circumstances traditional tools weren't an option. Below I will go over functionality, benefits, things to be aware of, etc. If you are already tired of reading this, you can grab the source code or compiled tool from my github here: https://github.com/anthemtotheego/SharpExec
Current modules:
When running the PSExec and SMBExec modules, please be aware that these are extremely noisy. There will be a ton of log activity, so if you are testing a mature organization and your goal is not to get caught, you don't want to run these. Unfortunately though, many organizations still don't catch this type of activity and in most cases you are probably fine running these modules. For a great rundown on how these types of tools work, check out this great blog series by @ropnop - https://blog.ropnop.com/using-credentials-to-own-windows-boxes/
Like other tools with similar functionality, administrative rights are required.
Examples:
I have always been a fan of individuals who provide clear examples of using their tools and what behavior I should expect over the here is a tool, I wish you the best of luck approach. So in this section I have tried to supply screenshots of various examples of using SharpExec. Feel free to reach out to me on twitter @anthemtotheego if something doesn't make sense or is confusing. This goes for any of my projects.
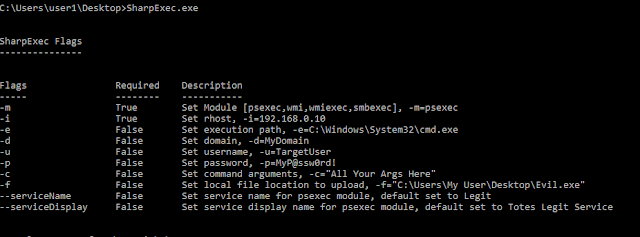
Running SharpExec without any arguments prints the help menu
The below example starts a semi-interactive shell to a remote domain joined system from a non-domain joined system using the WMIExec module
The below example starts a semi-interactive shell as user1 on the remote system using no username/password and then uses the get command available within the WMIExec/SMBExec modules to download a file from the remote system's current directory to your local system
The below example starts a semi-interactive shell as NT Authority\System on the remote system using no username/password and then uses the put command available within the WMIExec/SMBExec modules to upload a file from your local system to the remote system
The below example uploads the local binary noPowershell-noargs.exe to the remote system's C:\ drive and executes the binary via the WMI module. It then waits for the user to press Enter before removing the file off of the remote system
The below example uses the PSExec module to execute a PowerShell Empire payload on the remote system via cmd.exe. This will spawn a PowerShell Empire shell running as NT Authority\System
The below example uses the tool SharpCradle.exe to pull SharpExec.exe into memory and execute the WMIExec module to gain a semi-interactive shell on the remote system
Conclusion:
Hopefully this has been a good tutorial on a few ways to use SharpExec. Till next time and happy hacking!
Link to tools:
SharpExec - https://github.com/anthemtotheego/SharpExec
SharpExec Compiled Binaries - https://github.com/anthemtotheego/SharpExec/tree/master/CompiledBinaries
SharpCradle GitHub - https://github.com/anthemtotheego/SharpCradle
SharpExec is an offensive security C# tool designed to aid with lateral movement. While the techniques used are not groundbreaking or new by any means, every environment is different and what works for one situation might not work for the next. This tool is a combination of code I have been using over the years when needing to move laterally in a Windows environment and due to various circumstances traditional tools weren't an option. Below I will go over functionality, benefits, things to be aware of, etc. If you are already tired of reading this, you can grab the source code or compiled tool from my github here: https://github.com/anthemtotheego/SharpExec
Current modules:
- WMIExec - Semi-Interactive shell that runs as the user. Best described as a less mature version of Impacket's wmiexec.py tool.
- SMBExec - Semi-Interactive shell that runs as NT Authority\System. Best described as a less mature version of Impacket's smbexec.py tool.
- PSExec (like functionality) - Gives the operator the ability to execute remote commands as NT Authority\System or upload a file and execute it with or without arguments as NT Authority\System.
- WMI - Gives the operator the ability to execute remote commands as the user or upload a file and execute it with or without arguments as the user.
- In the future I would like to add lateral movement through DCOM and pass the hash functionality
- Doesn't need to be supplied credentials if the current user running the program has the appropriate permissions (admin rights) to other remote systems. This can come in handy when you compromise a system but don't have valid credentials yet.
- The tool itself can be easily executed in memory, for example, using Cobalt Strike or SharpCradle.
- Tools that are similar can behave differently enough that one tool's behavior gets flagged while the other one doesn't.
- Sometimes you just don't feel like dealing with SSH tunneling or port forwarding just to run a specific tool and having other options is great.
When running the PSExec and SMBExec modules, please be aware that these are extremely noisy. There will be a ton of log activity, so if you are testing a mature organization and your goal is not to get caught, you don't want to run these. Unfortunately though, many organizations still don't catch this type of activity and in most cases you are probably fine running these modules. For a great rundown on how these types of tools work, check out this great blog series by @ropnop - https://blog.ropnop.com/using-credentials-to-own-windows-boxes/
Like other tools with similar functionality, administrative rights are required.
Examples:
I have always been a fan of individuals who provide clear examples of using their tools and what behavior I should expect over the here is a tool, I wish you the best of luck approach. So in this section I have tried to supply screenshots of various examples of using SharpExec. Feel free to reach out to me on twitter @anthemtotheego if something doesn't make sense or is confusing. This goes for any of my projects.
Running SharpExec without any arguments prints the help menu
The below example starts a semi-interactive shell as user1 on the remote system using no username/password and then uses the get command available within the WMIExec/SMBExec modules to download a file from the remote system's current directory to your local system
The below example starts a semi-interactive shell as NT Authority\System on the remote system using no username/password and then uses the put command available within the WMIExec/SMBExec modules to upload a file from your local system to the remote system
The below example uploads the local binary noPowershell-noargs.exe to the remote system's C:\ drive and executes the binary via the WMI module. It then waits for the user to press Enter before removing the file off of the remote system
The below example uses the tool SharpCradle.exe to pull SharpExec.exe into memory and execute the WMIExec module to gain a semi-interactive shell on the remote system
Conclusion:
Hopefully this has been a good tutorial on a few ways to use SharpExec. Till next time and happy hacking!
Link to tools:
SharpExec - https://github.com/anthemtotheego/SharpExec
SharpExec Compiled Binaries - https://github.com/anthemtotheego/SharpExec/tree/master/CompiledBinaries
SharpCradle GitHub - https://github.com/anthemtotheego/SharpCradle





Comments
Post a Comment