Finding Hidden Treasure on Owned Boxes: Post-Exploitation Enumeration with wmiServSessEnum
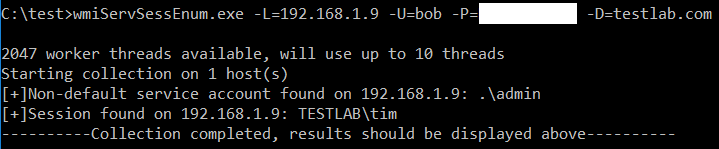
TLDR: We can use WMI queries to enumerate accounts configured to run any service on a box (even non-started / disabled), as well as perform live session enumeration. Info on running the tool is in the bottom section. Link to Github: https://github.com/G0ldenGunSec/wmiServSessEnum Background On a recent engagement I had gotten local admin privileges on ~20 boxes, and after querying active sessions on them got me nothing interesting I was ready to look for other potential escalation paths. I ran secretsdump against several of the systems to grab local account hashes, and found that in the process of running it, I had also obtained plaintext credentials for a domain account that was not mentioned in any of the session enumeration information I had pulled. This got me thinking about how this was possible, as well as how I could more reliably hunt for similar configurations on other systems I could remotely execute code on. First, to explain what was go...
